Ransomware Group REvil Demands $70 Million In Kaseya Cyberattack
(CBS) - Over the Fourth of July weekend, Russia-linked cybercriminals claim they infected more than a million systems globally with ransomware. The full scope of the attack is still unfolding after more than a thousand companies found their data encrypted on Friday in what could be largest ransomware spree in history.
The attack targeted Kaseya VSA, a software used by more than 36,000 customers, including managed service providers (MSPs). Many small to medium-sized businesses hire MSPs to oversee their IT infrastructure.
Kaseya CEO Fred Voccola said in an interview that 50-60 customers were affected, including nearly 40 MSPs. For each MSP targeted, there are dozens of companies at risk of compromise.
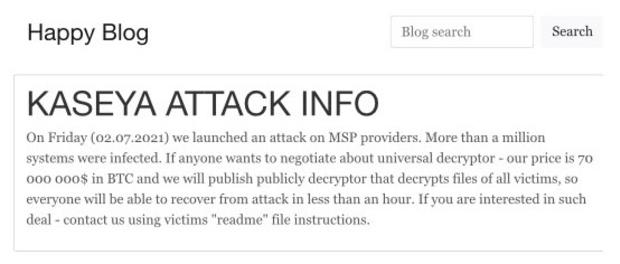
In a blog post on Sunday night, the ransomware group REvil offered the victims a universal decryption tool in exchange for a lump sum payment of $70 million in Bitcoin.
Dutch security researchers were aware of the Kaseya vulnerability before Friday's cyberattack. A software patch was already made but hadn't yet been distributed, according to Victor Gevers, chair of the Dutch Institute for Vulnerability Disclosure. It's still unclear how REvil learned of the exploit before a patch was released.
BleepingComputer reports REvil also issued a base ransom demand of $5 million for MSPs and $45,000 for individual companies.
"It's possible that companies which decide to negotiate the demand may find themselves facing delays due to the possibly unprecedented number of simultaneous negotiations that REvil will need to handle. It's simply another obstacle that victims may need to deal with," said Brett Callow, threat analyst at cybersecurity firm Emsisoft.
REvil, also known as Sodinokibi, provides malware kits for affiliates to launch cyberattacks in exchange for a cut of the profit. The Ransomware-as-a-Service (RaaS) operation is behind some of the largest known extortion threats, including $42 million from entertainment law firm Grubman Shire Meiselas & Sacks.
In June, meat producer JBS paid REvil $11 million in Bitcoin after a ransomware attack halted operations at more than a dozen meatpacking plants, including the company's North American headquarters in Greeley.
The timing of Friday's ransomware attack before the holiday weekend could be part of REvil's strategy. JBS became aware of its ransomware attack over Memorial Day weekend, when employees were more likely to take time off.
"Organizations can't prevent these kinds of attacks completely, but with the right execution they can detect fast and react fast in order to make the attack in general not very interesting to the attackers," explained Reuven Aronashvili, founder of Israeli cybersecurity firm CYE. "It's an extortion model so if the attackers can't gain access to something an organization finds valuable, then there won't be a pay day."
Supply chain cyberattacks have become increasingly common. The SolarWinds attack, detected in late 2020, began with a corrupted software update that allowed Russian spies to access 18,000 government and private computer networks. In a meeting last month, President Joe Biden warned Russian President Vladimir Putin that the U.S. will "take action" if Russia continues to harbor cybercriminals or engage in hacking attacks.
The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency are working with Kaseya to address the cyberattack. In a statement, Deputy National Security Advisor Anne Neuberger said President Biden directed the full resources of the government to investigate the hack. The FBI said it may not be able to respond to each victim individually, however, due to the scale of the attack.
In a security advisory, Kaseya recommended customers immediately shut down their VSA server to prevent the attack from spreading. The company is working with the incident response firm FireEye and plans to release a patch for on-premise customers. In the meantime, Kaseya released a self-assessment tool so that companies can determine whether they were affected.
Kaseya said all on-premise VSA servers should remain down until further notice. Customers who receive communication from the attackers should not click on any links, Kaseya said, because they could be "weaponized."
Software-as-a-Service customers were never at risk, according to Kaseya. The company set a goal to bring datacenters online by Monday evening. For updates, visit kaseya.com/potential-attack-on-kaseya-vsa.
RELATED: 'Following The Money': The Rapid Rise Of Ransomware & How To Defend Against It